Have a Question?
Qubes on the Vault
Qubes Overview
Qubes is a Linux distribution operating system that emphasizes security and follows an open-source approach. It effectively employs Xen-based virtualization to establish isolated virtual machines through Paravirtual (PV) or Hardware Virtual Machine (HVM) virtualization techniques. These virtual machines, known as "qubes," are designed to mitigate the potential damage in case of compromise by segregating them into distinct security domains. For instance, separate qubes (VMs) are dedicated to insecure browsing, work-related tasks, and personal use and data, with each assigned a specific level of trust.
Qubes offers various additional features, including:
- Support for multiple operating systems such as Debian, Fedora, and Windows.
- Ability to create disposable VMs.
- Integration with Whonix, enhancing privacy and anonymity.
- Robust security for private keys through Split GPG.
Qubes adopts a hierarchical trust model comprising five levels to differentiate between operating functions based on their level of safety and trustworthiness. The levels range from "Safe and ultimately trusted" (level 5) to "Unsafe and untrusted" (level 1). The trust levels assigned to different components in Qubes are as follows:
- Xen Hypervisor, AdminVM: level 5
- GuiVM, TemplateVMs, AppVM2: level 4
- Sys-firewall VM: level 3
- AppVM1 (OS & user applications): level 2
- sys-USB VM, Sys-net VM: level 1
For more information please refer to the Qubes website here
Verify Hardware Requirements
Qubes has very specific hardware requirements which can be found here. Successful installation has been accomplished on our FW6D, FW6E, VP4630, VP4650 and VP4670 which support VT-d and VT-x.
Note: With UEFI BIOS, legacy mode must be selected. Coreboot is also supported by Qubes.
Install Qubes
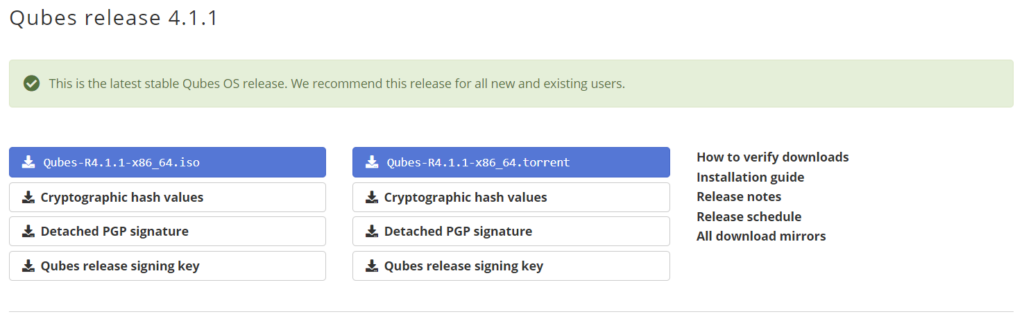
As of 8/2022, Qubes 4.1.1 is the most recent release and can be downloaded here. Note: Qubes 4.0.4 and all prior releases up to Qubes 4 including 3.2.1, 3.1, 3.0, live USB (alpha), Qubes 2 and Qubes 1 are all old and unsupported releases and Qubes strongly advise upgrading to 4.1.1 in order to receive the latest security updates.
Qubes 4.1.1 can be downloaded here
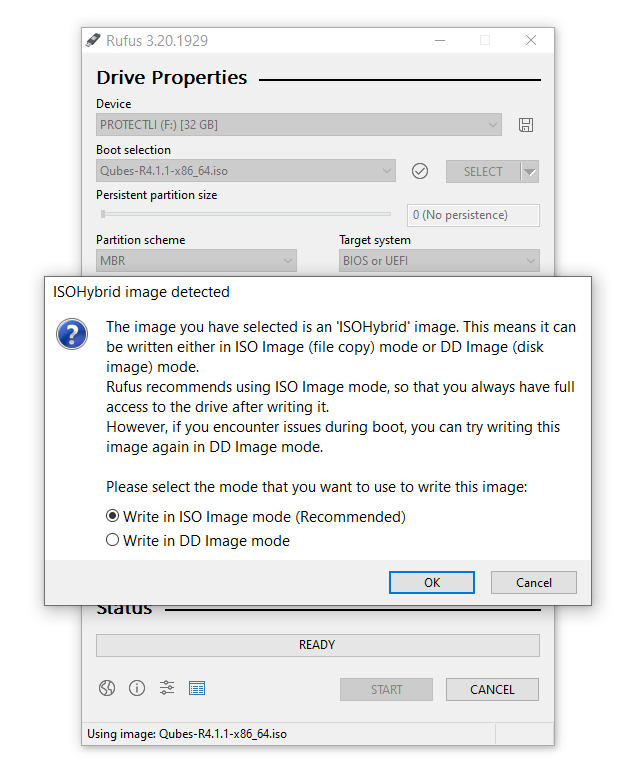
Burn the Installation Image to a USB Drive
An easy way to create a bootable USB device is to use software such as balenaEtcher or Rufus. With Rufus, please note that it must be written in DD image mode.
Note: For a link on how to create a bootable USB please refer to our Knowledge base Article here
Install the Operating System on the Vault
Once the Qubes installation USB drive has been created, it is ready to be installed on the Vault.
- Verify the Vault is powered down.
- Verify the monitor is connected.
- Verify the USB keyboard is plugged in.
- Verify an Ethernet connection is in the "WAN" port that is connected to a DHCP server.
- Insert the USB install drive into a USB port on the Vault.
- While powering up the Vault, press "F11" key until it boots to the BIOS and you see the boot options screen.
- Select the USB drive to boot from.
- On the boot screen, select the Test this media & install Qubes option.
- When the installer screen appears, select your language preference.
- On the Installation summary screen, select appropriate installation configuration settings for Localization, Software, System, Root Account and User Account for installation destination. Select Done after making selections.
- Enter a passphrase for disk encryption (optional)
- Select Begin Installation.
- After installation is complete, select Reboot.
- Enter your encryption passphrase when prompted (if added during installation).
- At the Initial Setup screen, select Qubes OS. This creates the initial qubes. There are a number of defaults already selected. For an option description, please refer to the Qubes Install Guide here.
- Select Done after making configuration selection and this will start the final process.
- After the configuration is done, this ends the final Qubes installation process.

*The Qubes website provides additional information for install and can be found here
Qubes Compatibility
Qubes has been successfully installed on the Protectli Vaults.
| Vault | Latest Version Tested | AMI BIOS | coreboot |
|---|---|---|---|
| FW2B | Not supported | Not supported | Not supported |
| FW4A | Not supported | Not supported | Not supported |
| FW4B | Not supported | Not supported | Not supported |
| FW6A | Qubes Release 4.1.1 | Not supported | Not supported |
| FW6B | Qubes Release 4.1.1 | Not supported | Not supported |
| FW6C | Qubes Release 4.1.1 | Not supported | Not supported |
| FW6D | Qubes Release 4.1.1 | Tested | Tested |
| FW6E | Qubes Release 4.1.1 | Tested | Tested |
| VP4630 | Qubes Release 4.1.1 | Tested | Tested |
| VP4650 | Qubes Release 4.1.1 | Tested | Tested |
| VP4670 | Qubes Release 4.1.1 | Tested | Tested |
| VP2410 | Not supported | Not supported | Not supported |
| VP2420 | TBD | TBD | TBD |