Have a Question?
OpenVPN Performance on The Vault
OpenVPN Performance
Overview
Depending on individual use cases, different hardware firewalls may be useful for different types of network applications and as such, Protectli offers different hardware with varying capabilities. Frequently, it is useful for a customer to know the performance characteristics of specific hardware before making a decision to purchase. This article aims to provide a baseline of OpenVPN performance for several different Vaults, as tested in a lab environment, so the customer can make an informed decision as to what products best suit their needs.
Edit (10/12/2022): We will be updating this article with the latest version of pfSense and more specific settings. Until all results are current they will be marked in the table below.
Basic Performance
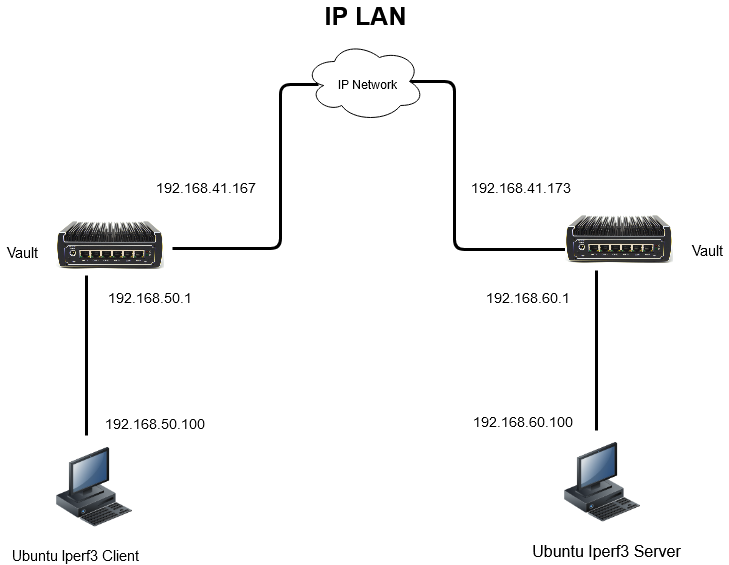
In a basic setup, The Vault is capable of routing packets at wire speed on all ports for all models. For a 1 Gbps ethernet interface, the actual data throughput is ~940 Mbps due to overhead in an IP packet. The test network consists of 2 computers running Ubuntu 20.04.1 version of Linux and 2 Vaults running pfSense® CE version 2.4.5_1. One of the Ubuntu computers is running iperf3 as a server, the other is running iperf3 as a client.
OpenVPN
OpenVPN is a popular protocol that is used to authenticate and encrypt/decrypt packets to provide secure transport of packets through the network. An OpenVPN "tunnel" encrypts the entire packet, not just the payload, and is commonly used to create Virtual Private Networks (VPN).
Configuring OpenVPN
When configuring OpenVPN tunnels (and other secure connections) multiple parameters must be configured. The set of parameters is known as a "cipher suite". The main parameters for OpenVPN consist of an Encryption method and a Message Authentication method. The configuration must be identical at each end of the tunnel in order to make a connection. With OpenVPN, one side of the tunnel is the "server" and the other end is the "client". Multiple clients can be connected to a single server for a hub and spoke type of architecture.
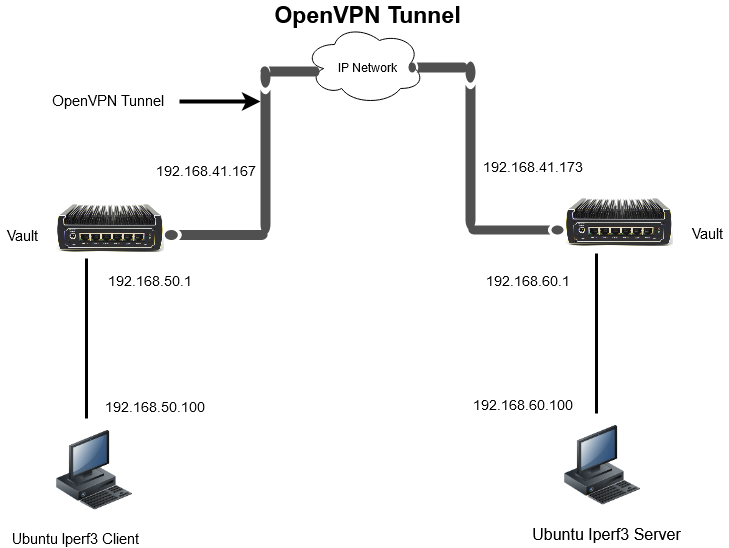
The diagram below shows an OpenVPN tunnel. The difference between the LAN example above and the OpenVPN tunnel is that the entire packet is encrypted "end-to-end" between the Vault/Firewalls and the data can travel through the network securely.
OpenVPN Performance
Adding an OpenVPN tunnel introduces "overhead" which is added when a packet enters a tunnel and stripped off when a packet leaves the tunnel. This process adds additional data to each packet, but is not part of the payload. Therefore, when running performance measurement tests, the indicated traffic throughput will be less than throughput achieved without an OpenVPN encrypted tunnel. In addition to the pure impact on the payload due to additional overhead, the device that adds the overhead must also encrypt the data. Similarly, the device at the other end of the tunnel receiving the packet must decrypt the data before sending it onward. Encryption and decryption of the packet requires significant processing power and affects the throughput of the devices. The latest versions of The Vault include Intel’s AES-NI hardware support which facilitates faster encryption/decryption with less impact on CPU performance. The performance varies depending on the parameters of the many different cipher suites. For example, a cipher suite that uses AES128 may perform better than AES256 due to easier encryption/decryption. It would be difficult if not impossible to test all possible cipher suites. For this purpose, a variety of different iterations have been tested, including ones that are not optimal in terms of performance, or commonplace. In order to test performance, pfSense® CE 2.4.5_1 was installed on the Vaults and OpenVPN tunnels were configured with the following initial cipher suite which provided the most optimal results found across all platforms:
- AES128 bit encryption algorithm with 128 bit blocks using the Cipher Block Chaining mode (CBC) operation
- Secure Hash Algorithm (SHA) 256 bit Message Authentication
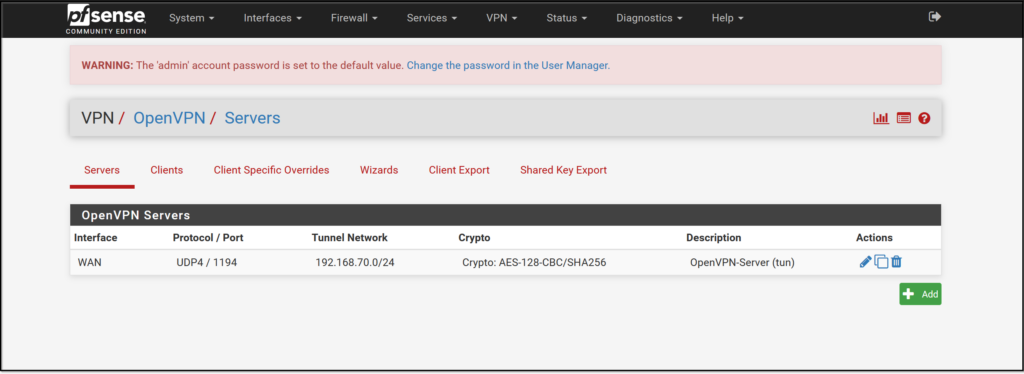
The main configuration page for VPN->OpenVPN->Servers is shown below.
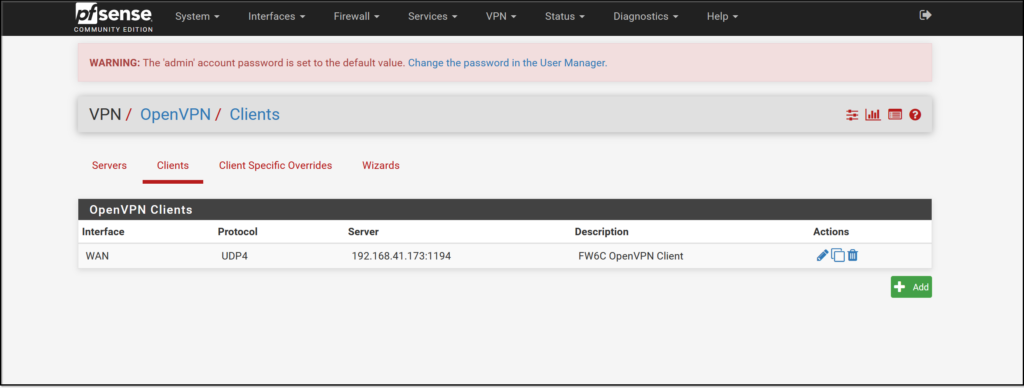
The main configuration page for VPN->OpenVPN->Clients is shown below.
In this example, data from LAN network 192.168.50.0 is "tunneled" to LAN network 192.168.60.0 over the WAN interface. In the reverse direction, data from LAN network 192.168.60.0 is "tunneled" to LAN network 192.168.50.0 over the WAN interface. The results of performance tests run on the Vaults are shown in the table below.
For more detailed information on the performance results, please click on the following link: OpenVPN Performance Sheet
| Vault Model | Unencrypted (Mbps) "#iPerf3 -c -P4 -f m" | IPSec (pfSense) AES-128-GCM/AES-XCBC/ AES128-GCM "#iPerf3 -c -P4 -f m" | IPSec (OPNsense) 128 bit AES-GCM w/ 128 bit ICV/AES-XCBC/14 [2048 bits] DH/AES128gcm16/No Hash/14 [2048 bits] PFS "#iPerf3 -c -P4 f m" | OpenVPN (pfSense 2.7) AES-256-GCM/SHA256 (Mbps) "#iPerf3 -c -P4 -f m" | WireGuard (OPNsense wireguard-go) 256-bit ChaCha20Poly1305 Avg (Mbps) "#iPerf3 -c -P4 -f m" |
|---|---|---|---|---|---|
| FW2B | ~940 | ~520 | ~529 | ~114 | ~280 |
| FW4B | ~940 | ~635 | ~747 | ~134 | ~290 |
| FW4C | ~2300 | ~807 | ~167 | ~315 | |
| FW6A | ~940 | ~875 | ~785 | ~491 | ~876 |
| FW6Br2 | ~940 | ~875 | ~814 | ~850 | ~907 |
| FW6C | ~940 | ~875 | ~821 | ~816 | ~907 |
| FW6D | ~940 | ~875 | ~879 | ~894 | ~909 |
| FW6E | ~940 | ~875 | ~879 | ~906 | ~909 |
| VP2410 | ~940 | ~875 | ~809 | ~371 | ~733 |
| VP2420 | ~2330 | ~1700 | ~1320 | ~450 | ~1200 |
| VP4630 | ~2340 | ~2100 | ~1790 | ~1240 | ~2100 |
| VP4650 | ~2340 | ~1900 | ~1910 | ~1290 | ~2160 |
| VP4670 | ~2340 | ~1900 | ~2200 | ~1360 | ~2200 |
Conclusions on OpenVPN Performance
OpenVPN is a critical set of protocols used to provide secure communication through the Internet. There are many different cipher suites that can be used depending on the requirements of the user. The configuration used may impact the performance and therefore the throughput of the devices in the network. This tutorial is an aid to selecting the best Vault for your application. If you have any questions, feel free to reach out to us! You can submit a ticket here, find more information in our Knowledge Base, or visit the pages at IETF as reference.
