Have a Question?
Full Disk Encryption with BitLocker & dTPM
Overview
Computers are a part of everyday life. We use them for planning our day, paying our bills, and reading our emails. As more of our lives become digital the risk of data falling into the wrong hands grows. Threat actors continue to employ ever more sophisticated methods of breaching networks and systems, but thankfully, we have ever more sophisticated defenses to help thwart such attacks. One such feature is Bitlocker, which is built into Windows, and encrypts data, preventing data theft from lost, stolen, or inappropriately decommissioned computers. To get the most out of BitLocker on a Protectli Vault, we recommend using a Trusted Platform Module (TPM). The Vault Pro series is compatible with Protectli TPM.
This guide will walk through the initial setup of BitLocker and the Group Policy settings that further strengthen BitLocker's security.
Background: Bitlocker & TPM
Bitlocker makes use of Advanced Encryption Standard (AES) to secure your data. AES is a National Institute of Standards and Technology (NIST) standard for encryption. AES is a powerful encryption methodology and it is used by the United States Government to secure classified information. AES utilizes a symmetric-key algorithm, which means it uses one private key to encrypt and decrypt data.
- Bitlocker uses a TPM to securely store the private keys and verify the integrity of the storage device.
- There are two types of TPMs relevant to Bitlocker and the Vault. fTPM and dTPM.
- fTPM refers to a firmware TPM. fTPMs run in the CPU's trusted execution environment (TEE), guaranteeing the integrity of code and data.
- Intel, AMD, and Qualcomm have their own versions of fTPM.
- Intel’s fTPM implementation is called PTT. Protectli Vaults that run Intel CPU’s with PTT can make use of PTT via the optional AMI BIOS
- At this time, PTT is only available on the VP4600 series Vaults.
- Intel, AMD, and Qualcomm have their own versions of fTPM.
- dTPM or discrete TPM refers to a physical microcontroller directly attached to the motherboard either soldered down or via module.
- dTPMs are considered more secure because it is an isolated device separate from the rest of the computer. The chance for both devices to be compromised is much lower than one system being compromised.
- fTPM refers to a firmware TPM. fTPMs run in the CPU's trusted execution environment (TEE), guaranteeing the integrity of code and data.
For more information about TPM please review our TPM on the Vault Knowledge Base article.
Prerequisites
- Verify your Vault is from the Vault Pro lineup (VP2410/2420, VP4630/4650/4670)
- Verify Windows 10 or Windows 11 is installed on your Vault
- Verify your Vault is equipped with a dTPM or PTT
- Verify the Vault is powered down
- Verify the HDMI is connected to a monitor
- Verify the USB keyboard and mouse are plugged in
- Power on the Vault
- Press Delete during boot to bring up the BIOS menu
- Verify the BIOS menu is displayed
- For AMI BIOS
- Select Advanced
- Select Trusted Computing
- Verify TPM2.0 Device Found
- For coreboot BIOS
- Select Device Manager
- Select TCG2 Configuration
- Verify Current TPM Device reads TPM2.0
Edit Group Policy
By default, BitLocker uses AES 128bit encryption. Editing the group policy settings will allow us to use a stronger encryption algorithm. In this example, we use 256bit encryption.
- Power on the Vault
- Log into Windows
- Type 'Edit Group Policy' into Windows Search
- Navigate to BitLocker Drive Encryption
- Administrative Templates > Windows Components >BitLocker Drive Encryption.
- Select Local Group Policy Editor to expand the file tree
- Verify Local Group Policy Editor window opens on the right
- Select Administrative Templates to expand the file tree
- Verify the Administrative Templates page opens on the right
- Select Windows Components to expand the file tree
- Verify Windows Components opens on the right
- Select BitLocker Drive Encryption
- Verify BitLocker Drive Encryption opens on the right
- Administrative Templates > Windows Components >BitLocker Drive Encryption.
- Select Choose drive encryption method and cipher strength.
- Be sure to select the option that matches your Windows version.
- Verify the choose drive encryption method and cipher strength group policy window opens
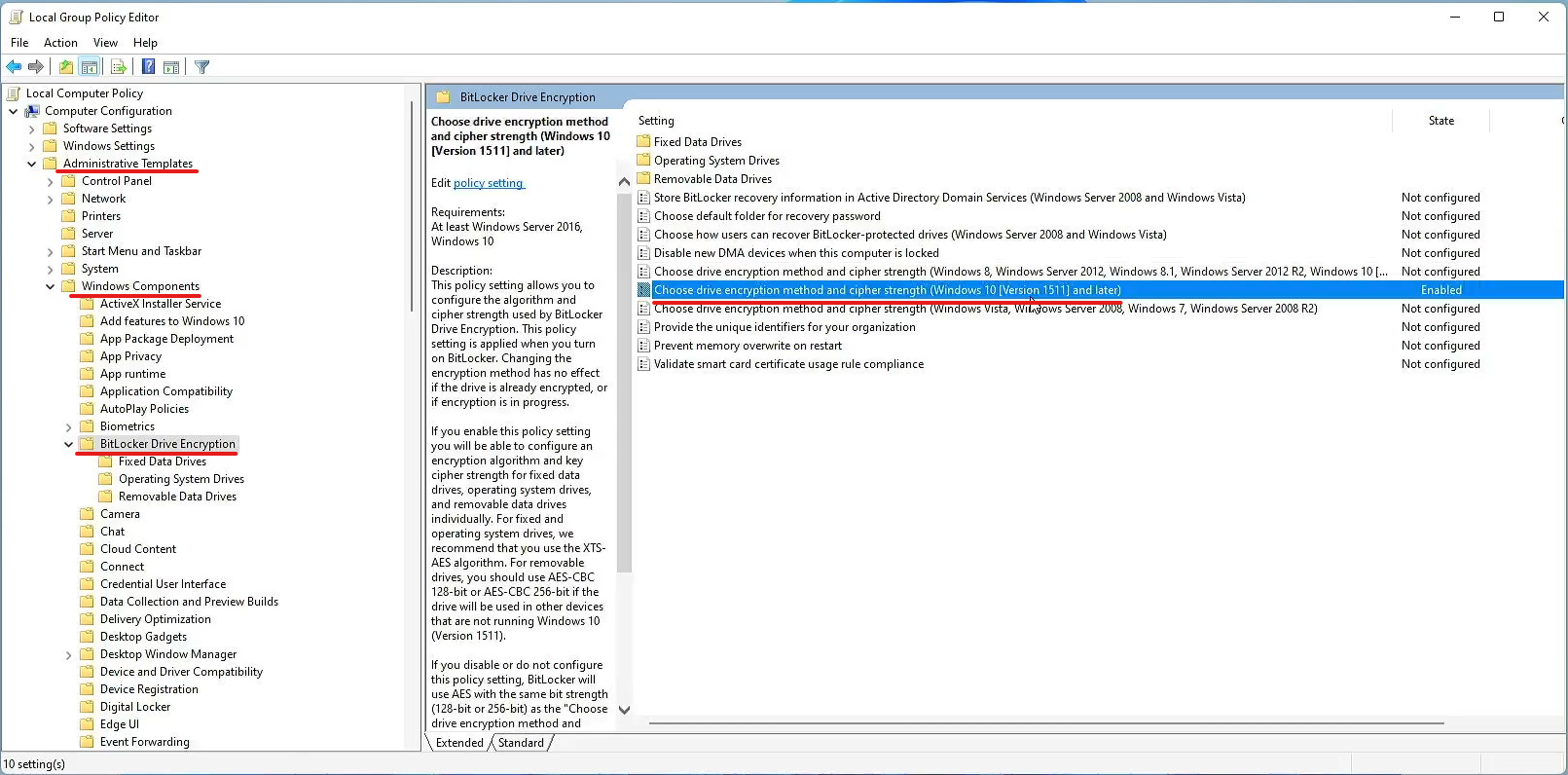
- Select Enable the group policy.
- Verify the button next to Enable is filled
- Select the method of encryption.
- AES 128bit is selected by default, in this example, we use 256bit encryption.
- The OS drive, fixed drives, and removable drives can be encrypted, in this example, we encrypt the OS and fixed drives.
- Double-check your settings
- Select Apply
- Select OK
- Reopen the window to verify the settings have been applied
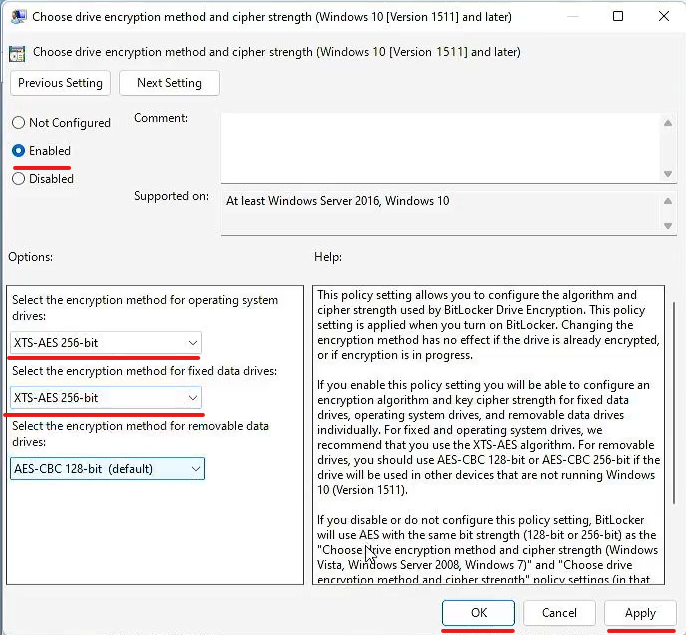
Verify TPM
- Type 'tmp.msc' into Windows Search
- Verify TPM Administration window opens
- Verify the Status, your TPM is ready for use
You are now ready to enable BitLocker!
Enabling BitLocker
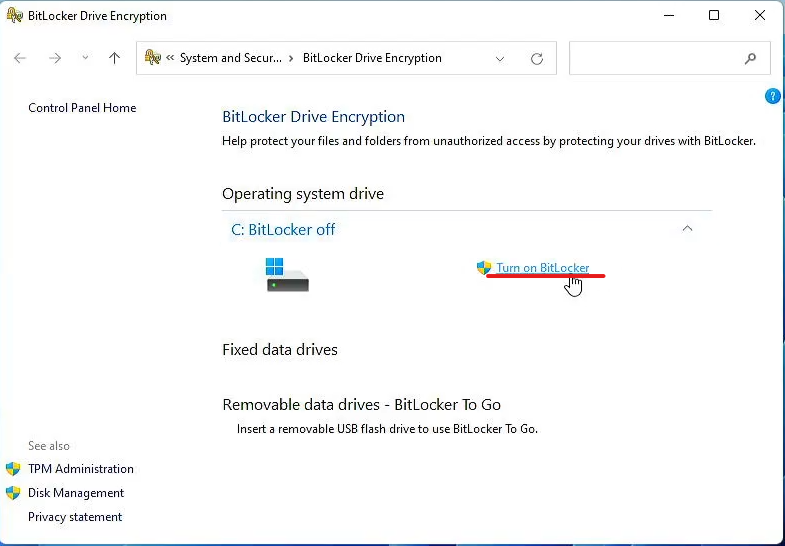
- Type Manage BitLocker into the Windows Start Menu
- Select BitLocker Drive Encryption
- Verify BitLocker Drive Encryption window opens
- Select Turn on BitLocker
- Verify the BitLocker Drive Encryption setup window opens
- Be sure to save a backup of your recovery key
- In this example, we save the recovery key to a USB drive
- Insert a USB drive into your computer
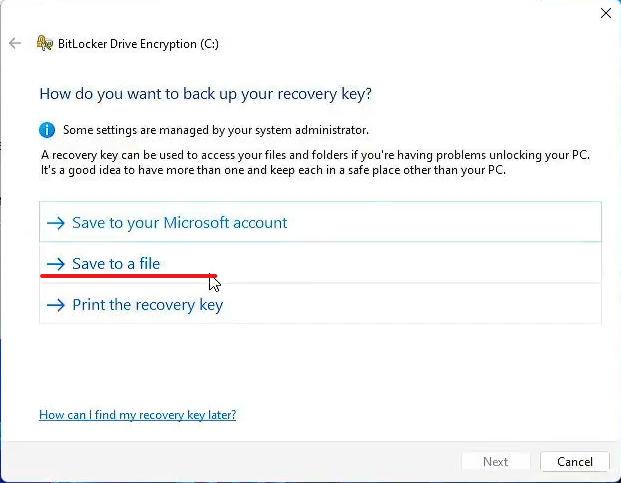
- Select Save to a file
- Verify File Explorer opens
- Select the USB drive
- Select Save
- Verify the window closes
- Select Next
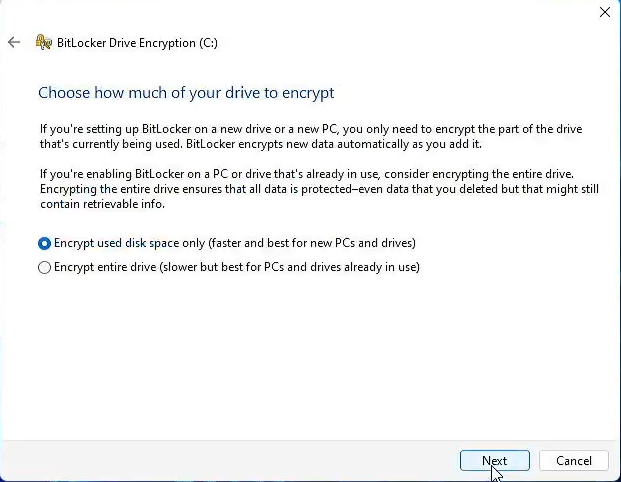
- Select Encrypt used disk space only if you are encrypting on a new PC or drive
- Select Encrypt entire drive if you have already been using this PC or drive
- Verify your selection is marked by the blue dot
- Select Next
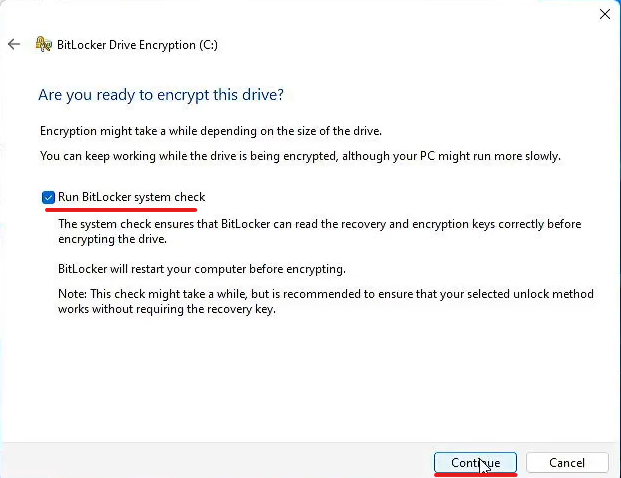
- Select Run BitLocker system check
- Verify the selection box is checked blue
- Select Continue
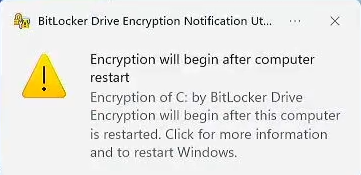
- Reboot your PC to begin encryption
- Navigate back to BitLocker Drive Encryption
- Type Manage BitLocker into the Windows Start Menu
- Select BitLocker Drive Encryption
- Verify BitLocker Drive Encryption window opens
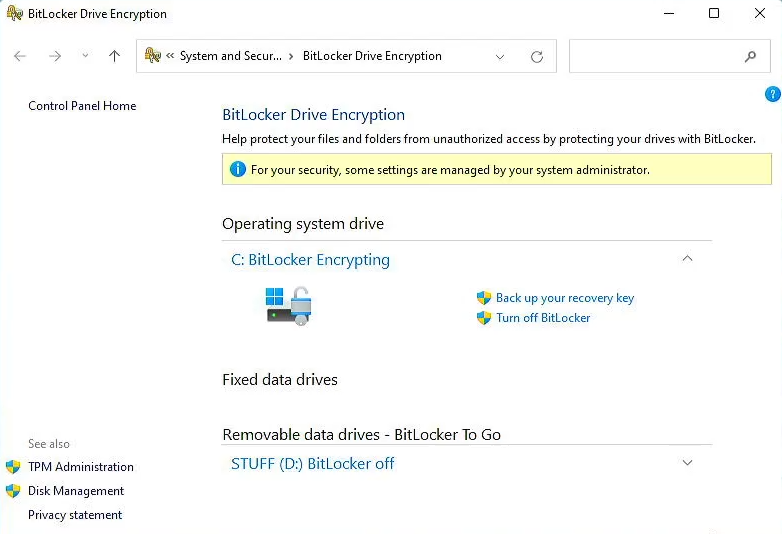
- Verify BitLocker is encrypting
- This will take time depending on the size of the drive, what you chose to encrypt, and your cipher strength
- Windows can still be used while the drive is encrypting but performance will be reduced
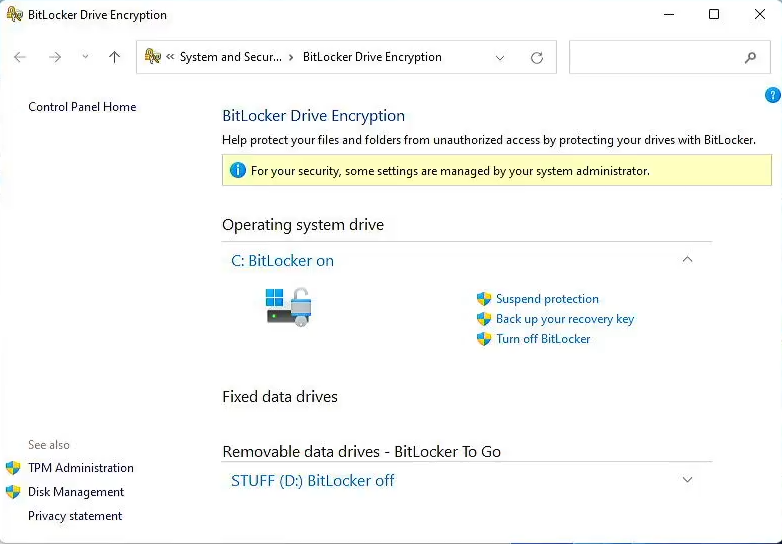
Congratulations, your drives are now encrypted with BitLocker, your keys are saved on a TPM for seamless access, and your recovery keys are stored safely in case of emergency.
As always, if you have any questions, feel free to contact support at support@protectli.com
